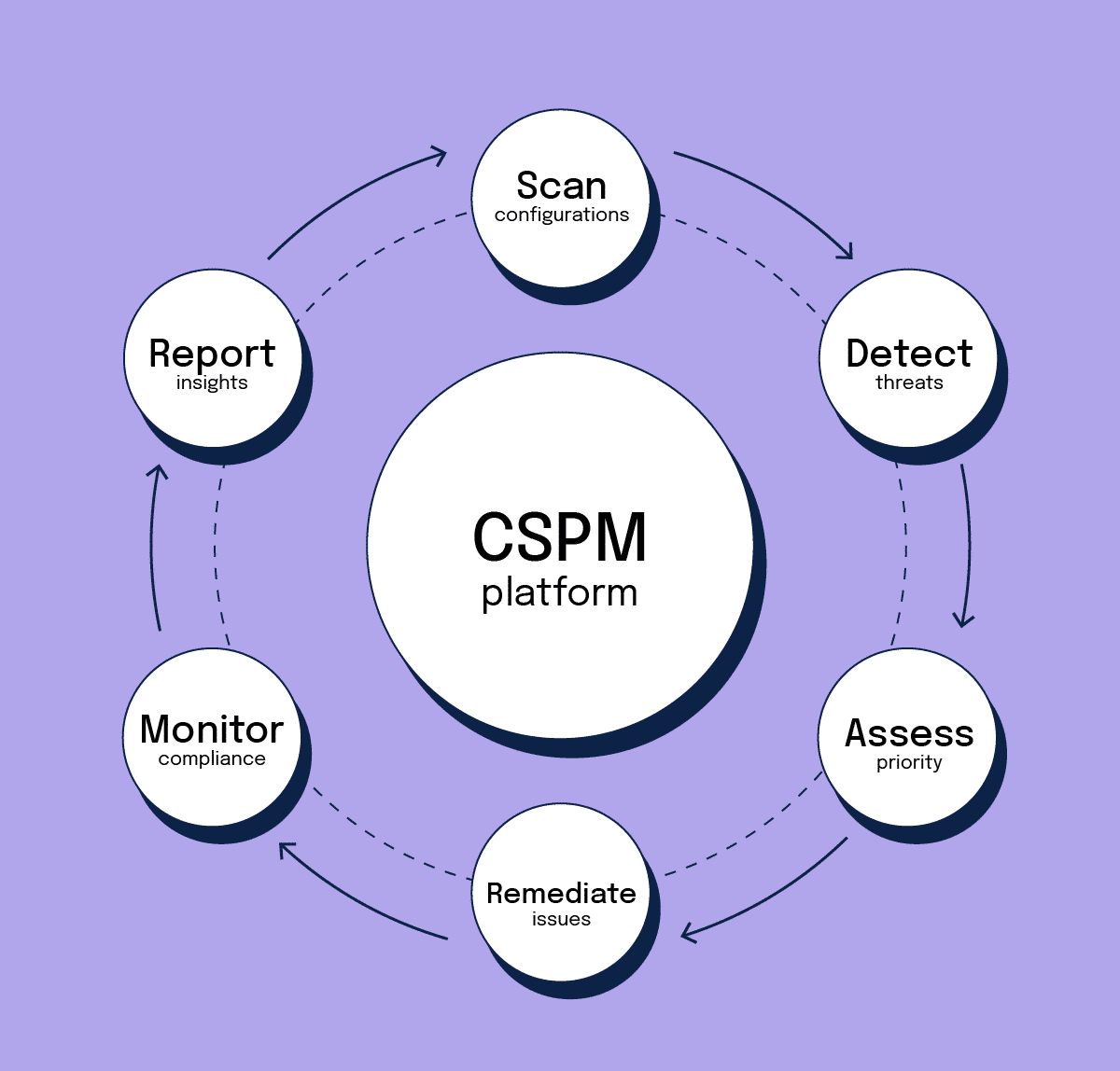
I’ll go over the top cloud security posture management platforms in this post, which assist businesses in finding configuration errors, upholding compliance, and lowering security threats in cloud environments.
These technologies support current DevOps and cloud-native operations while offering continuous visibility, automated monitoring, and risk prioritization to efficiently safeguard multi-cloud infrastructures.
Why Use Cloud Security Posture Management Platforms
Detect Cloud Misconfigurations: Continuously find unsecured settings, exposed elements, and fragile configurations in the cloud.
Ensure Regulatory Compliance: Monitor and implement compliance of the standards, i.e., CIS, PCI DSS, GDPR, HIPAA, and ISO.
Reduce Security Risks: Identify and resolve high-priority security issues before potential threats can exploit them.
Improve Cloud Visibility: Attain centralized visibility for AWS, Azure, GCP, and the hybrid-cloud environments.
Automate Security Controls: Set security policies and automated alerts to lessen the need for manual efforts.
Support DevOps & Cloud-Native Security: Integration with CI/CD pipelines and Infrastructure as Code for shift-left security
Prevent Configuration Drift: Systematically monitor and fix modifications to prevent vulnerabilities in cloud security posture.
Key Point & Best Cloud Security Posture Management Platforms List
| Platform | Key Points |
|---|---|
| Palo Alto Networks Prisma Cloud | Unified CSPM, CWPP, and CIEM platform with AI-driven risk prioritization, multi-cloud visibility, IaC scanning, and compliance automation |
| Check Point CloudGuard CSPM | Strong compliance monitoring, automated remediation, posture management across AWS, Azure, GCP, and native integration with Check Point security ecosystem |
| Sophos Cloud Optix | AI-powered risk visibility, misconfiguration detection, threat intelligence correlation, and seamless integration with Sophos cloud security stack |
| Fortinet FortiCWP | Agentless cloud workload visibility, continuous compliance monitoring, native Fortinet Security Fabric integration, and real-time threat detection |
| Orca Security CSPM | Agentless deep cloud visibility, prioritizes risks based on attack paths, rapid deployment, and strong asset context without performance impact |
| Wiz Cloud Security | Cloud-native, agentless platform with full-stack visibility, attack path analysis, fast onboarding, and strong vulnerability correlation |
| Sysdig Secure + CSPM | Runtime security combined with CSPM, Kubernetes-focused visibility, compliance-as-code, and real-time threat detection |
| Aqua Security CSPM | Focused on container and Kubernetes security, posture management for cloud-native workloads, shift-left security, and compliance automation |
| Microsoft Defender for Cloud | Native Azure CSPM with multi-cloud support, continuous security recommendations, compliance scoring, and deep Microsoft ecosystem integration |
| AWS Security Hub + Config | Centralized AWS security posture management, continuous configuration monitoring, compliance checks, and native AWS service integrations |
1. Palo Alto Networks Prisma Cloud
Prisma Cloud by Palo Alto Networks. Within a single platform, Palo Alto Networks Prisma Cloud combines CSPM, CWPP, and CIEM for a holistic and unified approach to cloud security. Identifying and removing visibility blind spots across multi-cloud environments like AWS, Azure, and GCP. Obtaining, automating, and keeping compliance reports without exception.

With Prisma Cloud, Palo Alto Networks Prisma Cloud eases the process of complicated cloud environments by removing the burden of keeping secure configurations and baseline policies to mitigate risks automated and at scale. Machine learning and planning contextual risk prioritization processor.
Palo Alto Networks Prisma Cloud Features, Pros & Cons
Features
- Integrated CSPM, CWPP, & CIEM functionality
- Visibility across many clouds (AWS, Azure, GCP)
- Automated compliance frameworks and reporting
- Context aware risk prioritization
- IaC scanning with DevOps integration
Pros
- Comprehensive security across all products
- Excellent compliance and audit functionality
- Effective risk reporting and noise reduction
- DevOps/CI pipeline integration
- Strong visibility across cloud environments
Cons
- Initial complexity of configuration
- Licensing costs may be high for SMBs
- Learning curve for the more advanced features and functionality
- Potential training needs for effective utilization
- Large inventories may incur moderate local resource overhead
2. Check Point CloudGuard CSPM
Check Point CloudGuard has been specifically designed to assist security teams in shifting left to monitor and enforce Cloud best practices over their multi-cloud environments.

Check Point CloudGuard CDN correlates configuration drift to identify risk before it get exploited. Check Point CloudGuard integrates with the native Cloud APIs as part of the larger Check Point Infinity architecture to enforce policies across workloads, networks, and identities.
CloudGuard’s automation provides compliance alerting and remediation in real-time. For security and DEVOPS CloudGuard provides the visibility and collaboration to continuously monitor cloud risk and configure the controls needed to improve the security posture.
Check Point CloudGuard CSPM Features, Pros & Cons
Features
- Continuous posture monitoring
- Compliance assessment dashboards
- Automated remediation capabilities
- Integration with cloud-native services
- Multi-cloud policy enforcement
Pros
- Strong policy enforcement capabilities
- Good compliance framework support
- Integration with Check Point security tool suite
- Real-time alerts and monitoring
- Effective risk visualization
Cons
- UI can be hard for inexperienced users
- Suggests remediation that may need tuning
- May give incorrect alerts
- Needs specialist personnel to navigate it
- Limited integration with non-Check Point tools
3. Sophos Cloud Optix
The Sophos Cloud Optix platform makes use of AI for cloud security, visibility, and to assist organizations in identifying problematic configurations, underutilised resources, and potentially dangerous permissions spread across their cloud accounts.

This solution uses threat intelligence to correlate potentially dangerous configurations with threat activity in order to better manage misconfiguration threats. Sophos Cloud Optix operates in AWS, Azure, and GCP environments. It serves to automate compliance monitoring in the areas of CIS, PCI DSS, and GDPR.
It makes available damage control response in an automated fashion within security and DevOps infrastructures to facilitate response workflows. Cloud Optix aids in the proactive cloud posture management, attack surface minimization, and active compliance in a low maintenance work environment, by providing seamless onboarding and consolidated risk visibility for teams.
Sophos Cloud Optix Features, Pros & Cons
Features
- Automated risk detection with AI
- Automated misconfiguration scanning
- Correlation of multiple threat intelligence
- Customized dashboards for compliance
- Automated workflows for remediation
Pros
- Seamless onboarding and deployment
- Enhanced accuracy from AI risk prioritization
- Dashboards are simple and intuitive.
- Ecosystem of Sophos
- Compliance reporting is useful
Cons
- Lack of in-depth analysis for vulnerabilities
- Policy customization isn’t as sophisticated
- Remediation workflows could be improved.
- Lacks an abundance of Enterprise functionalities
- Advanced analytics might be absent
4. Fortinet FortiCWP
Fortinet FortiCWP (Cloud Workload Protection) provides complete posture management, and risk detection in order to protect cloud workloads and the associated native services. Fortinet FortiCWP provides continuous visibility and control in the AWS, Azure, and GCP environments and instantly enacts policies to eliminate misconfigurations, compliance gaps, and potential attack vectors.

Using the Fortinet Security Fabric, Fortinet improves visibility and response coordination to incidents by integrating with firewalls, endpoint security, and network security.
FortiCWP also provides real-time analytics and alerts that assist users in attempting to ensure compliance and to contain isolated high risk workloads in the environment. Its agentless design improves the level of protection against configuration drift and cloud native threats to workloads, and also simplifies the deployment.
Fortinet FortiCWP Features, Pros & Cons
Features
- Cloud workload security without agents.
- Continuous posture evaluation
- Risk detection and alerts
- Integration with Fortinet Security Fabric
- Compliance reporting
Pros
- Excellent integration for workload security.
- Visibility of alerts and risks is good.
- Compatible with Fortinet ecosystem.
- Agentless and operates lightly.
- Models are compliance ready.
Cons
- Fortinet users have the best experience.
- Advanced CSPM analytics are less.
- Configurable policies can be complex.
- Smaller third-party integration ecosystem.
- More intuitive interface is desired.
5. Orca Security CSPM
Orca Security CSPM is a leader in agentless cloud security, offering the ability to scan entire cloud environments, workloads, configurations, and data stores without the need to install a software agent on every asset.

With contextual and analytical vulnerability awareness, Orca Security CSPM alerts organizations on risk and prioritized response based on exploitable attack vectors and the associated attack path. Orca CSPM’s cloud API access facilitates seamless integration for automated cloud resource and risk discovery on AWS, Azure, and GCP.
The platform also cross-correlates risk relating to identity and access, which reduces alert fatigue and enables security teams to take alerts seriously. Orca is especially effective in its cloud security risk mitigation providing organizations the ability to address their most pressing and exploitable attack vectors first.
Orca Security CSPM Features, Pros & Cons
Features
- Scanning of the cloud without using an agent.
- The detection of deep and misconfigured settings are found.
- Attack path-based prioritization
- Continuous multi-cloud monitoring
- Identity and access risk insights
Pros
- Instantaneous deployment without agents
- Strong focus on false positive mitigation
- Great contextual risk and visibility
- Discovery of cloud assets is quick
- Well-suited for hybrid and multi-cloud
Cons
- High cost of licensing
- Some complex environments require additional tuning
- Automation for remediation is limited
- Training is necessary for advanced features
- Custom policies require support tailored to them
6. Wiz Cloud Security
Wiz Cloud Security delivers award-winning full-spectrum cloud security with no agents required that consolidates CSPM, vulnerability management, and threat detection into one single workflow.
Wiz Cloud Security provides visibility into multi-cloud environments for cloud misconfigurations, exposed services, and insecure identities, by continuously ingesting and analyzing data from cloud provider APIs.

Wiz Cloud Security’s attack path modeling illustrates how historians of disparate risks can be stitched together by an adversary, allowing teams to prioritize mitigations based on actual exploit paths.
Wiz also offers Infrastructure as Code (IaC) scanning and several compliance frameworks that empower DevOps and security teams to shift left. Wiz strengthens posture management by speeding up risk reduction with rapid implementation and integrated visibility.
Wiz Cloud Security Features, Pros & Cons
Features
- Total visibility with no cloud agents
- Attack path algorithms
- Scanning Infrastructure as Code and Compliance
- Risk Prioitization
- Threat Detection and Alerting
Pros
- Seamless integration and quick onboarding
- Quality attack path visibility
- Context around the vulnerabilities is strong
- Offers an overview of multi-cloud environments in one console
- Appropriate services for the initial stages of Cloud DevOps integration
Cons
- Larger estates can have prohibitive pricing
- User experience can be daunting if more complex
- Alerting systems do require tuning to be effective
- Some advanced dashboards require significant skill
- Suggestions for remediation differ based on cloud provider
7. Sysdig Secure + CSPM
The combination of Sysdig Secure + CSPM offers additional runtime protection and container protection which is especially applicable within Kubernetes and other cloud native environments. Users get risk visibility on misconfiguration, policy ineffectiveness, and runtime threats spread across clusters and cloud services.

Users of Sysdig Secure + CSPM can set compliance requirements as code and automate continuous validation of resources to those guardrails.
With the integration of runtime detection and response, the system narrows focus to active threats and correlated posture imbalances to improve the detection and response times. Container behavior and process analytics further enable security teams to rapidly respond to the enforcement of best cloud native practices and uncover security events.
Sysdig Secure + CSPM Features, Pros & Cons
Features
- CSPM + Runtine security
- Focus on Kubernetes and containers
- Compliance as Code
- Risk detection and alerting
- DevOps intergation
Pros
- Excellent for cloud-native workloads
- Combines posture and runtime protection.
- Good for Kubernetes environments.
- Flexible compliance enforcement.
- Integrates with CI/CD tools.
Cons
- Best suited for container workloads.
- Complexity in feature setup.
- Resource overhead in large environments.
- Icons and UI have learning curve.
- Some features need premium plans.
8. Aqua Security CSPM
Aqua Security CSPM also focuses on cloud native security and offers the protection of applications and containers while supporting the posture of Kubernetes deployments. Aqua Security CSPM also identifies misconfigurations, compliance gaps, and risky entitlements across cloud accounts and container environments.

Its shift left capabilities scan IaC templates and registries and even prior to deployment, capture issues that may get to production. Aqua Security CSPM provides its users with considerable contextual analysis to act upon prioritized risks while supporting fully autonomous or manually guided action.
It also integrates security controls across DevOps and CI/CD environments, setting up orchestrated security actions. Compliance with target governance frameworks is assured through continuous enforcement of framework requirements on the underlying infrastructure and workloads. This also narrows risk perimeter in dynamic cloud native environments.
Aqua Security CSPM Features, Pros & Cons
Features
- Cloud-native posture scanning.
- IaC and registry scanning.
- Compliance automation.
- Risk detection and alerts.
- DevOps pipeline integration.
Pros
- Strong \”shift-left\” security
- Great for container/K8s security
- Continuous compliance tracking
- Customizable policy controls
- Integrates with pipelines well
Cons
- Focused more on cloud-native vs general CSPM
- Limited multi-cloud heavy features
- Can require tuning
- Not as strong on CIEM features
- Larger deployments need expertise
9. Microsoft Defender for Cloud
Microsoft Defender for Cloud (once referred to as Azure Security Center) assists with securing hybrid and multi-cloud environments with continual posture review and assessment providing recommendations and compliance scoring.

Through Azure, AWS and GCP integration, Microsoft Defender for Cloud identifies misconfigurations, insecure network settings, and identity vulnerabilities, as well as offers integrated workflow with Microsoft Defender threat detection services and adaptive threat protection.
Teams get to monitor compliance dashboards to keep track of regulatory standards. Defender for Cloud provides organizations a unique blend of automated security posture improvement and hardening with integrated security to cloud operations.
Microsoft Defender for Cloud Features, Pros & Cons
Features
- Continuous posture assessment
- Native Azure security integration
- Multi-cloud support
- Threat protection and alerts
- Compliance dashboards
Pros
- Native integration with Azure & Microsoft tools
- Good compliance reporting
- Built-in recommendations and remediation
- Easy to onboard for Azure customers
- Supports AWS & GCP
Cons
- Some advanced features need higher tiers
- Plenty of options in the UI can become overwhelming.
- AWS/GCP have less depth than Azure.
- Dependency with Microsoft ecosystem.
- Not much room for custom policy tuning.
10. AWS Security Hub + Config
This integrated solution provides centralized security posturing via integration with various AWS services. AWS Security Hub + Config automation includes an audit structure. It includes coverage for assessing compliance reporting violating control regulations in multiple security services offered by AWS.

Alerts for non-compliance rule accesses are automated via linked services such as AWS Config and Stream Guard. Security teams can manage risk by defining compliance within governance frameworks such as the CIS control set where appropriate. Security Hub and Config units within the AWS virtual services ecosystem offer significant operational simplicity by allowing automated insight generation and risk mitigation via differentiated dashboard reporting and actionable risk findings.
AWS Security Hub + Config Features, Pros & Cons
Features
- AWS has unified security posture.
- Compliance with no manual effort.
- Configuration is monitored over time.
- GuardDuty and IAM Analyzer integration.
- Findings in one place.
Pros
- Native integration with AWS.
- Compliance with multiple rules is strong.
- Drift detection is constant.
- Synergy with ecosystem of AWS services.
- Alerts and analytics consolidated.
Cons
- Only supports workloads in AWS.
- More tools needed for remediation workflows.
- Limited to services that are AWS-native.
- Alerts can be excessive.
- More advanced knowledge is needed for custom policies.
Conclusion
Selecting the finest Cloud Security Posture Management systems is crucial for preserving visibility, compliance, and control across multi-cloud infrastructures in today’s quickly changing cloud environments.
Prominent solutions including Prisma Cloud, Wiz, Orca Security, Microsoft Defender for Cloud, and AWS Security Hub assist enterprises in continuously identifying misconfigurations, minimizing attack surfaces, and using contextual analytics to prioritize threats.
These technologies allow security and DevOps teams to proactively secure cloud assets by integrating automation, compliance monitoring, and real-time threat correlation. In the end, the top Cloud Security Posture Management systems enable companies to grow safely, uphold legal compliance, and fortify their whole cloud security plan.
FAQ
Cloud Security Posture Management (CSPM) refers to tools and practices that continuously monitor cloud environments to detect misconfigurations, enforce security best practices, ensure compliance, and reduce risk across cloud services. CSPM platforms help organizations maintain secure cloud configurations and meet regulatory standards.
CSPM solutions are essential because cloud environments are highly dynamic and complex. Misconfigurations, excessive permissions, and compliance violations can lead to security breaches. CSPM platforms provide visibility, automated checks, and remediation guidance to protect cloud workloads and data.
Some of the best CSPM solutions include Palo Alto Networks Prisma Cloud, Check Point CloudGuard CSPM, Sophos Cloud Optix, Fortinet FortiCWP, Orca Security CSPM, Wiz Cloud Security, Sysdig Secure + CSPM, Aqua Security CSPM, Microsoft Defender for Cloud, and AWS Security Hub + Config.
Yes. Most CSPM platforms offer continuous compliance monitoring against frameworks such as CIS Benchmarks, PCI DSS, GDPR, HIPAA, and NIST, generating dashboards and reports to simplify audits and governance.
Many modern CSPM tools support multi-cloud environments, including AWS, Azure, and Google Cloud Platform, enabling a unified security view for hybrid or multi-cloud deployments.